IP booters have emerged as popular tools among cyber attackers seeking to overwhelm target systems. An IP booter operates by coordinating multiple compromised computers, servers, and IoT devices into a botnet network. When activated, these systems simultaneously send data packets to the target IP address. The flood of incoming traffic exceeds the target’s capacity to process legitimate requests, leading to service outages.
Technical Components of IP Booter Attacks
The attack process involves several key elements:
- Command and control servers managing the botnet
- Amplification techniques using DNS or NTP protocols
- Traffic routing through compromised proxy servers
- Automated scripts coordinating attack timing
- Network stress testing tools repurposed for attacks
Common IP Booter Methods
Script kiddies often employ these attack variations:
- UDP Flood Attacks
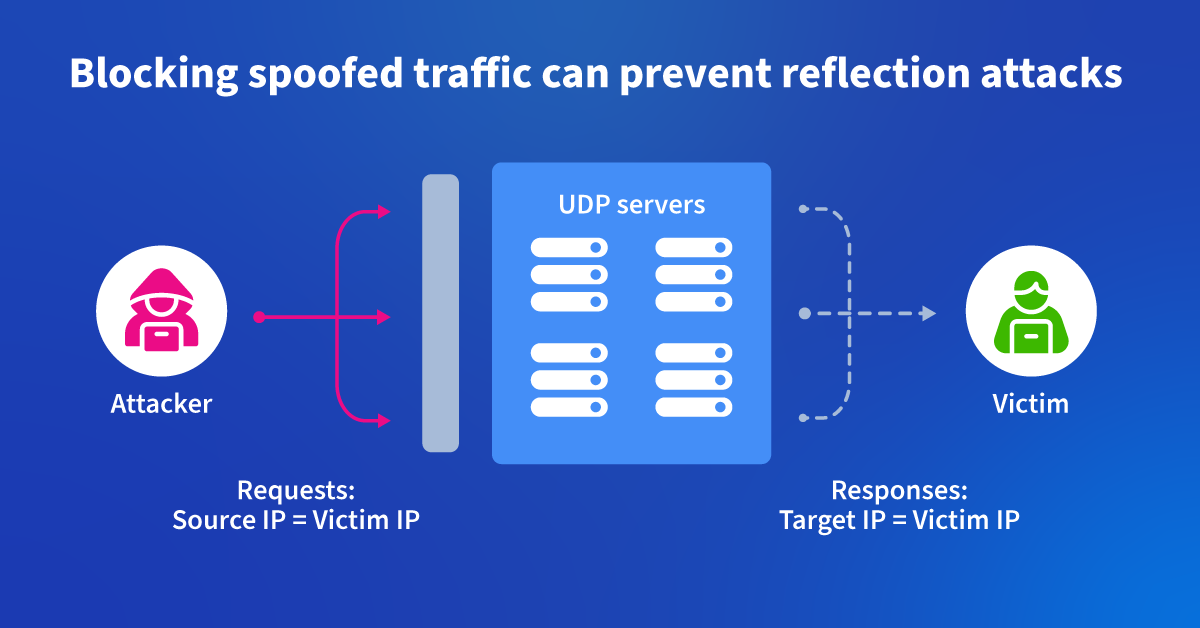
The attacker sends numerous UDP packets to random ports, forcing the target to repeatedly check for listening applications and reply with ICMP packets until resources are depleted.
- SYN Flood Attacks
By initiating many TCP connections without completing the handshake, attackers can quickly consume the target’s connection queue and memory.
- HTTP Flood Attacks
Attackers generate countless HTTP GET or POST requests, overwhelming web servers trying to process the incoming traffic.
Protection Against IP Booter Attacks
Organizations can implement several defensive measures:
- Deploy dedicated DDoS mitigation appliances
- Configure network firewalls to filter attack traffic
- Use content delivery networks for traffic distribution
- Monitor network traffic patterns for early detection
- Maintain adequate bandwidth and server capacity
Impact on Target Systems
IP booter attacks can cause:
- Complete service unavailability
- Slow website performance
- Lost revenue during outages
- Damaged business reputation
- Wasted IT resources
Evolution of Attack Tools
Modern IP booters offer advanced capabilities:
- User-friendly web interfaces
- Customizable attack parameters
- Multiple attack methods
- Progress monitoring dashboards
- Target status verification
Botnet Infrastructure
The effectiveness of IP booters relies on:
- Vast networks of compromised devices
- Distributed attack sources
- Automated coordination
- High-bandwidth connections
- Continuous recruitment of new bots
Detection and Response
Security teams should focus on:
- Real-time traffic analysis
- Pattern recognition
- Source IP blocking
- Rate limiting
- Traffic scrubbing
Attacker Motivations
Common reasons for IP booter usage include:
- Competitive advantages
- Personal vendettas
- Political activism
- Financial extortion
- Testing system limits
Future Trends
The IP booter landscape continues changing with:
- More sophisticated attack methods
- Larger botnets
- Improved automation
- Enhanced anonymity features
- Greater attack volumes
Technical Requirements
IP booter operations need:
- Command infrastructure
- Attack scripts
- Traffic generators
- Proxy networks
- Target monitoring
Mitigation Challenges
Organizations face difficulties like:
- Distinguishing attack traffic
- Managing mitigation costs
- Maintaining service quality
- Adapting to new threats
- Coordinating responses
Building Resilience
Critical preparation steps include:
- Regular stress testing
- Redundant systems
- Traffic filtering
- Resource scaling
- Incident response planning
An IP booter is a powerful tool used in DDoS testing that can help organizations assess their network resilience. Understanding what Is an IP Booter does allows companies to strengthen their defenses and ensure system availability and performance during potential threats.
Ongoing cat-and-mouse game between attackers and defenders drives continuous innovation in both offensive and defensive capabilities. Success requires staying informed about emerging threats while implementing robust security measures.